airodump-ng will display a list of detected access points, and also a list of connected clients (“stations”). Here's an example screenshot:
The first line shows the current channel, elapsed running time, current date and optionally if a WPA/WPA2 handshake was detected. In the example above, “WPA handshake: 00:14:6C:7E:40:80” indicates that a WPA/WPA2 handshake was successfully captured for the BSSID.
In the example above the client rate of “36-24” means:
- The first number is the last data rate from the AP (BSSID) to the Client (STATION). In this case 36 megabits per second.
- The second number is the last data rate from Client (STATION) to the AP (BSSID). In this case 24 megabits per second.
- These rates may potentially change on each packet transmission. It is simply the last speed seen.
- These rates are only displayed when locked to a single channel, the AP/client transmission speeds are displayed as part of the clients listed at the bottom.
- NOTE: APs need more then one packet to appear on the screen. APs with a single packet are not displayed.
| Field | Description |
|---|---|
| BSSID | MAC address of the access point. In the Client section, a BSSID of “(not associated)” means that the client is not associated with any AP. In this unassociated state, it is searching for an AP to connect with. |
| PWR | Signal level reported by the card. Its signification depends on the driver, but as the signal gets higher you get closer to the AP or the station. If the BSSID PWR is -1, then the driver doesn't support signal level reporting. If the PWR is -1 for a limited number of stations then this is for a packet which came from the AP to the client but the client transmissions are out of range for your card. Meaning you are hearing only 1/2 of the communication. If all clients have PWR as -1 then the driver doesn't support signal level reporting. |
| RXQ | Receive Quality as measured by the percentage of packets (management and data frames) successfully received over the last 10 seconds. See note below for a more detailed explanation. |
| Beacons | Number of announcements packets sent by the AP. Each access point sends about ten beacons per second at the lowest rate (1M), so they can usually be picked up from very far. |
| # Data | Number of captured data packets (if WEP, unique IV count), including data broadcast packets. |
| #/s | Number of data packets per second measure over the last 10 seconds. |
| CH | Channel number (taken from beacon packets). Note: sometimes packets from other channels are captured even if airodump-ng is not hopping, because of radio interference or overlapping channels. |
| MB | Maximum speed supported by the AP. If MB = 11, it's 802.11b, if MB = 22 it's 802.11b+ and up to 54 are 802.11g. Anything higher is 802.11n or 802.11ac. The dot (after 54 above) indicates short preamble is supported. Displays “e” following the MB speed value if the network has QoS enabled. |
| ENC | Encryption algorithm in use. OPN = no encryption,“WEP?” = WEP or higher (not enough data to choose between WEP and WPA/WPA2), WEP (without the question mark) indicates static or dynamic WEP, and WPA, WPA2 or WPA3 if TKIP or CCMP is present (WPA3 with TKIP allows WPA or WPA2 association, pure WPA3 only allows CCMP). OWE is for Opportunistic Wireless Encryption, aka Enhanced Open. |
| CIPHER | The cipher detected. One of CCMP, WRAP, TKIP, WEP, WEP40, or WEP104. Not mandatory, but TKIP is typically used with WPA and CCMP is typically used with WPA2. WEP40 is displayed when the key index is greater then 0. The standard states that the index can be 0-3 for 40bit and should be 0 for 104 bit. |
| AUTH | The authentication protocol used. One of MGT (WPA/WPA2 using a separate authentication server), SKA (shared key for WEP), PSK (pre-shared key for WPA/WPA2), or OPN (open for WEP). |
| ESSID | Shows the wireless network name. The so-called “SSID”, which can be empty if SSID hiding is activated. In this case, airodump-ng will try to recover the SSID from probe responses and association requests. See this section for more information concerning hidden ESSIDs. |
| STATION | MAC address of each associated station or stations searching for an AP to connect with. Clients not currently associated with an AP have a BSSID of “(not associated)”. |
| Rate | Station's receive rate, followed by transmit rate. Displays “e” following each rate if the network has QoS enabled. |
| Lost | The number of data packets lost over the last 10 seconds based on the sequence number. See note below for a more detailed explanation. |
| Packets | The number of data packets sent by the client. |
| Notes | Additional information about the client, such as captured EAPOL or PMKID. |
| Probes | The ESSIDs probed by the client. These are the networks the client is trying to connect to if it is not currently connected. |
NOTES:
RXQ expanded:
Its measured over all management and data frames. The received frames contain a sequence number which is added by the sending access point. RXQ = 100 means that all packets were received from the access point in numerical sequence and none were missing. That's the clue, this allows you to read more things out of this value. Lets say you got 100 percent RXQ and all 10 (or whatever the rate) beacons per second coming in. Now all of a sudden the RXQ drops below 90, but you still capture all sent beacons. Thus you know that the AP is sending frames to a client but you can't hear the client nor the AP sending to the client (need to get closer). Another thing would be, that you got a 11MB card to monitor and capture frames (say a prism2.5) and you have a very good position to the AP. The AP is set to 54MBit and then again the RXQ drops, so you know that there is at least one 54MBit client connected to the AP.
N.B.: RXQ column will only be shown if you are locked on a single channel, not channel hopping.
Lost expanded:
It means lost packets coming from the client. To determine the number of packets lost, there is a sequence field on every non-control frame, so you can subtract the second last sequence number from the last sequence number and you know how many packets you have lost.
Possible reasons for lost packets:
- You cannot send (in case you are sending) and listen at the same time, so every time you send something you can't hear the packets being transmitted in that interval.
- You are maybe losing packets due too high transmit power (you may be too close to the AP).
- There is too much noise on the current channel (other APs, microwave oven, bluetooth…)
Airmon-ng; Airodump-ng; Airbase-ng; Aireplay-ng; Airolib-ng; Aircrack-ng; and lots more; We will discuss about the tools above, as they are most frequently used tools and used in almost every Wireless Pentest. Aircrack-ng comes for Linux, Mac, and Windows and comes pre-installed in Kali Linux. We can manually install Aircrack-ng on Linux, Mac.
Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. Aircrack-ng 1.2 RC 2 Features. Once the download completes, you will have at your disposal a complete suite which provides different utilities. Aircrack ng comes with airdecap, airmon and airdriver. Most (not airmon-ng) aircrack-ng tools can be installed on macOS with MacPorts, but airodump-ng and aireplay-ng crash. So PLEASE, if you want to do other advanced networking things than network sniffing or what is described in this article, do yourself a favour and buy an USB adapter to use with the virtual machine. The following processes never affected airmon-ngso im puzzled (as always). Oh and I have the following version of Aircrack-ng: Aircrack-ng 1.2 rc1 r2459 - (C) 2006-2014 Thomas d'Otreppe. Found 5 processes that could cause trouble. If airodump-ng, aireplay-ng or airtun-ng stops working after a short period of time, you may want to kill (some of.
To minimize the number of lost packets, vary your physical position, type of antenna used, channel, data rate and/or injection rate.
Aircrack-ng (aircrack) is for wireless penetration testing, and it’s mighty fine. The aircrack site tells it best,
Airmon Ng Download
“Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools.”
The process of running aircrack can be a bit intricate. Took me close to a year to learn it, granted I do have interests outside of computers. But this post will set forth a beginning process for the Aircrack-ng suit. This will only cover airmon-ng, airodump-ng, for now.
NOTE: Macchanger [apt-get install macchanger] is a cool tool that changes MAC addresses.

# ifconfig wlan0 down
# macchanger -r wlan0 # Random MAC address
# ifconfig wlan0 down
Assumptions
Wireless Interface > wlan0
Monitor Mode Interface > mon0

The Process
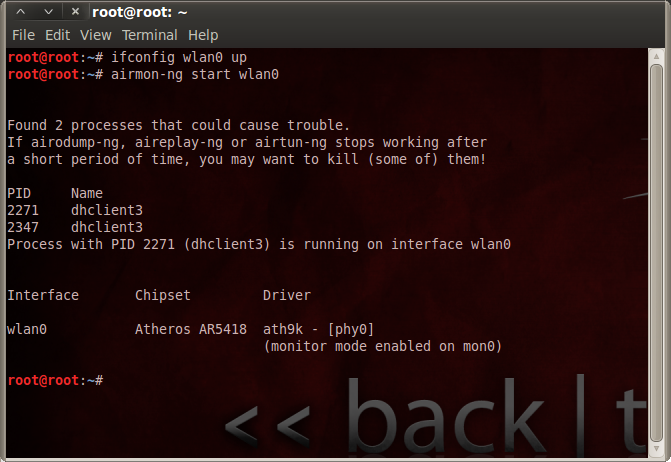
1) airmon-ng
Puts a device in monitor mode, virtually. This is where the device is listening, not associating with any networks. Always remember that the device put into monitor mode must also be taken out of monitor mode (airmon-ng stop mon0).
# iwconfig
# airmon-ng start wlan0
Below shows that the wlan0 was properly put into monitor mode.
2) airodump-ng
Airodump captures raw 802.11 frames (wireless), and it is recommended to run airodump-ng while running aircrack. This will speed up the process. Default output files are *.cap, *.csv, *.kismet.csv, and*.kismet.netxml.
# airodump-ng –beacons –showack -w ~/mmach/2013012401 mon0
Breakdown:
–beacons: Record all beacons in dump file
–showack: Print ack/cts/rts statistics
-w: File to write to
2013012401: I have a lot of files, so I had to develop a systematic approach to naming multiple files, while also remaining organized. Looks confusing at first, but it’s very simple– YEAR-MO-DY-NUM
mon0: The monitor interface
What it means…
For the purpose of demonstration,
N_1 > First row (BSSID PWR …)
These are the BSSID’s beaconing frames. In other words, these are the MAC addresses of networks within the location in which this scan was done. Also shown are,
PWR: Signal level. Turn up your frequency, and you’ll be seen far across your neighborhood. This is good in gauging the distance of a BSSID. Note that a value of ‘-1’ means your wireless driver does not support the signal level.
BEACONS: Beacon count
#Data: Number of packets captured
#/s: Number of packets per second
CH: Wireless channel
MB: Max speed supported by the access point (AP)
ENC: Encryption used (Surprisingly found a few WPA’s, and and open network)
CIPHER: Counter Cipher Mode with Block Chaining Message Authentication Code Protocol, wireless encryption protocol. These are the types: CCMP, WRAP, TKIP (commonly WPA), WEP, WEP40, or WEP104.
AUTH: Authentication type
ESSID: Extended Service Set Identifier, network name (Did you think it was ‘European Summer School on Industrial Dynamics’ for a minute?)
N_2 > Second (BSSID STATION …)
These are clients (devices) sending probes to ESSIDs (networks), trying to connect. So here, matching the the N_2 ‘BSSID’ column with the N_1 ‘BSSID’ column will show where a device is attempting to connect to.


STATION: Device
BSSID: Network. Where the device is trying to connect to.
E.G. N_2 (rows 7 & 8) end in ‘2E:80’. Match this with the N_1 ‘BSSID’, ..2E:80. This tells me that devices ..F3:A8 and ..1A:B2 are sending probes to the ..2E:80, ESSID of Jaroz.. and happens to be WPA (weak) encryption. Also judging by the ‘PWR’ value of -86 for all the above devices, in both N_1 and N_2, these devices are and equal distance. One device shows the ESSID in which it is probing, yet one doesn’t.
N_3 > Third (MAC CH …)
The ‘–showack‘ option provides this section. Here, same as step two- match up MAC addresses. So for the first column in N_3, we see in N_2 that MAC matches a device connecting to Dupke, ending in ..F7:F8. The lost packets number is high here.
Using tcpdump
# tcpdump -r 2013012401-01.cap | grep -e ‘Jarosz’
Reading packets are fun, but I’ll get into this more with the aircrack post, which will come soon.
2.1) Run aircrack (alongside airodump)
Airmon Download
Soon to come.
Airmon Ng For Mac Mojave
Contact me if you have any questions or feedback! @machn1k

Comments are closed.